I love collecting malicious emails, samples and trying to make sense of it, create context and share back with the community. One way I do so is by sharing malicious email attachments to MalwareBazaar and VirusTotal and including context such as email sender, subjects and date information. Since doing that, I have heard a few stories from other information security professionals, that were grateful for the information shared, as it helped them either retroactively search their own data or finding a malicious email when a malicious or suspicious binary is detected on an endpoint.
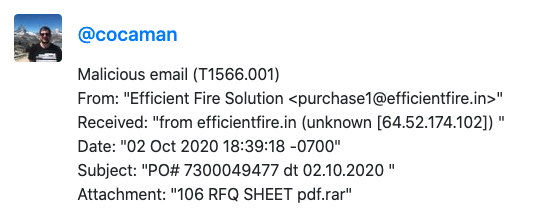
I want to make more use of my spam trap data and this weekend, my fellow research colleague and great inspiration, Twitter use @James_inthe_box published his monthly list of malicious emails that he saw during his collection. James has been sharing his lists for a long time and this weekend it clicked: I have the same data set and I can easily extract this from my spam traps. That being said, I sat down and created yet another Python script to check my mailboxes for all emails, extract the attachment, hash it and compare it to MalwareBazaar to see if the sample is malicious and if it is an identified threat. MalwareBazaar uses custom signatures to attribute a sample to a malware family, much more convenient than the various names vendors list for malware on VirusTotal.
How my script works:
- log into an IMAP mailbox
- searches for emails given a query
- fetch those emails
- download attachment
- create hash of the attachment (MD5 for now)
- query MalwareBazaar for any details
- export context information to a CSV file
Here is a recording of the script doing its task:
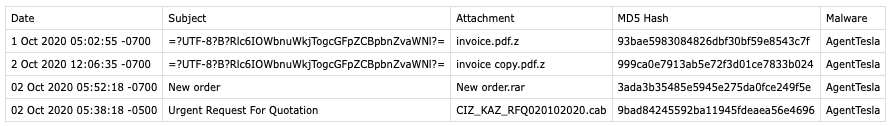
And here is the result CSV output:
You can download the script from my GitHub repository here: https://github.com/cocaman/analysis_scripts
Feel free to fork and send me pull requests (like adding lookups on other platforms, adding more fields for the CSV export, running custom scripts or Yara rules on the attachments). Just make sure to remove your credentials from the file. I am too lazy to come up with a nicer solution for this 😉
And yes, I am cheating a tiny bit, as I upload all the samples to MalwareBazaar during the month. This makes certain that my samples should be known and identified on the platform. If that is not a good reason for you to start sharing as well!