Today I came across a suspicious Word document when browsing Hybrid Analysis (which is always fun to see what is going on).
The document caught my eye for the single reason that it was called “swift message 1.docx” (c07fb4ab07e439463117cd7d060109cb814d928304e8828c3884ac2b88fece78). Since I work for a bank, I always have an urge to checkout banking related stuff (and we know that Swift definitely is banking related). After inspecting the stuff that Hybrid Analysis had extracted, we know the following:
- It is a Word document in the XML format
- The file does not contain a macro (docx can’t have macros)
- There seems to be an embedded object, but because the uploader didn’t share the sample, we can’t investigate this further
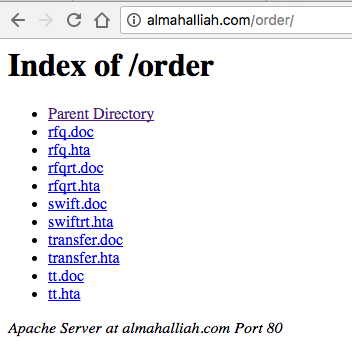
- The extracted files section shows a “.hta” and a “.doc” file
- This might be a sign of an old Office vulnerability (CVE-2017-0199) which might be exploited by this document.
- Checking the HTTP traffic we can see “winword.exe” proccess connecting to the host almahalliah[.]com / 192.254.235.79 and downloading another Word document (transfer.doc).
- The file is still available, as are other files.
Browsing the directory on the domain, we immediately see the directory content:

The domain age, the connect and a quick search indicated this must be a compromised domain. That provoked me to quickly send out a tweet.
no-no, not suspicious at all cc @malwrhunterteam @GoDaddyHelp @James_inthe_box @shotgunner101 @AilsaPanda pic.twitter.com/HK85YkLORl
— Corsin Camichel (@cocaman) September 16, 2017
I send a CC to several trusted users that helped me out in the past with other analyses. Shortly after, user @James_inthe_box wrote that this seems all to familiar. The different “.hta” files all downloaded an executable file. Such an executable was “hailrat.exe“. It is still unclear to me what exactly it is, the sandbox results aren’t very telling.
After all this, I started to get several replies from users in the MIddle East. Some of them from well connected users, such as @Voulnet, who started to propagate the information to other members and CERTs.
Let’s hope this helps to clean the domain and prevent further infections.
IOCs
dd1e76727368809ad5e1f65307c3df652d4d68b6eb01b682751053b7b1adad1c
c07fb4ab07e439463117cd7d060109cb814d928304e8828c3884ac2b88fece78
fb9425fb4b2e7d94edcb2588a948b9db0f515f091ff805778d128a43bec0412e
a5f73ba68139fcbfa07ef1cfaaec3b02f12ec5cb46e575592f73b67eb32a0f5f
bc6f3466621b273c22e984d830d88efd585e520d0b00cc92b68243476ad7d205
3e84bc7b495f3903ed98a114aa3dd20ca03aeb5199d9b2e7868a711091a7479e
almahalliah.com
192.254.235.79
Whois
Domain Name: ALMAHALLIAH.COM
Registry Domain ID: 414658039_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: http://www.godaddy.com
Updated Date: 2017-02-22T08:58:07Z
Creation Date: 2006-04-17T10:19:57Z
Registry Expiry Date: 2018-04-17T10:19:57Z
Registrar: GoDaddy.com, LLC