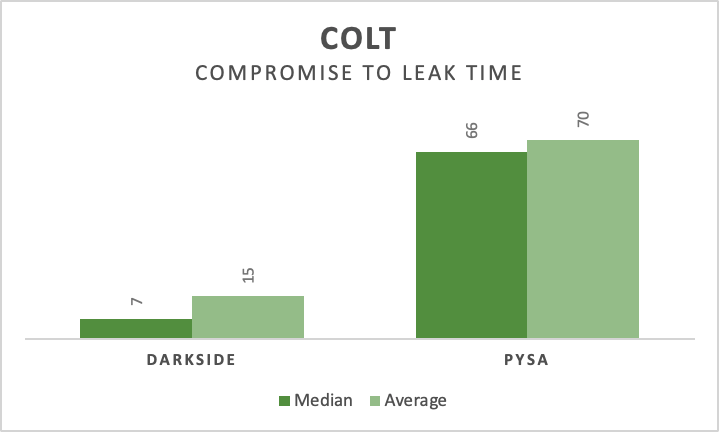
Ransomware, data theft and leaks. I do not plan on making this a ransomware-focused blog, but let us be honest, ransomware is just so prevalent that you cannot escape it. After my last blog and from private discussions, people working incident response cases in ransomware often are faced with the question: “When will the threat […]
Continue ReadingRansomware and Data Leak Site Publication Time Analysis
Learn at what times ransomware and data leak site operators are publishing victims on their dark web sites.
Continue ReadingObserved Malware Campaigns – October 2020
An output of my most recent script (see my post “Malicious Attachment Analysis Script“), is the ability to create statistics and the data-set to understand what kind of malware campaigns are being delivered by email attachments. In October 2020 I received a total of 76,888 emails (2,480 per day) to my spam traps. Obviously not […]
Continue ReadingMalicious Attachment Analysis Script
I love collecting malicious emails, samples and trying to make sense of it, create context and share back with the community. One way I do so is by sharing malicious email attachments to MalwareBazaar and VirusTotal and including context such as email sender, subjects and date information. Since doing that, I have heard a few […]
Continue ReadingMalwareBazaar by abuse.ch – Python Scripts
MalwareBazaar is a project operated by abuse.ch. The purpose of the project is to collect and share malware samples, helping IT-security researchers and threat analyst protecting their constituency and customers from cyber threats. abuse.ch MalwareBazaar Now that abuse.ch has launched their newest service, the MalwareBazaar I am very happy to share some of the python […]
Continue ReadingCelebrating The 100th Shared MISP Event
Today marks a big day for the security research and protection effort here at vulnerability.ch: We just created and shared our 100th event with the wider MISP community. Thanks to the inclusion of our research at the MISP community provided by CIRCL, we have been able to share and consume indicators of compromise (IOCs) from […]
Continue ReadingEconomics of “Sextortion” Mails
For the past few months (it started in July 2018), I have been collecting Bitcoin wallet addresses from so called “extortion” or “sextortion” emails. The addresses have been added to my MISP server and is shared with other researchers to investigate or detect additional mails. CIRCL now has used the data to generate an analysis […]
Continue Readingabuse.ch launches URLhaus, collection of malicious URLs
abuse.ch has recently launched a new project called “URLhaus”. URLhaus is a project with the goal of sharing malicious URLs that are being used for malware distribution. Anybody can register with a Twitter account and share malicious URLs they have detected. The system will download and analyse the payload (trying to identify it) and then […]
Continue ReadingFrom Russia with Love (and some help by Google)
Through some threat hunting on some OSINT platforms, I discovered a website hosting an image file named “image293.jpg” (6b872d1e949bd9d111168692301414bb685dc5c262ffae6f55f34c8041de0f5f VT | HA | ANY.RUN | Joe Sandbox). Trying to download the file shows that it is a redirect to Google’s short-url service goo.gl. From the link’s statistics page we can see that over 8500 redirects have been […]
Continue ReadingLinks of the Week 2018-01-04 (Meltdown & Spectre Special)
Vulnerability Site, Logo & FAQ Meltdown and Spectre CVE Numbers CVE-2017-5753 and CVE-2017-5715 => Spectre CVE-2017-5754 => Meltdown http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=2017-5715 http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=2017-5753 http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=2017-5754 Microsoft Patch January 3, 2018—KB4056892 (OS Build 16299.192) Red Hat Article Kernel Side-Channel Attacks – CVE-2017-5754 CVE-2017-5753 CVE-2017-5715 Google Project Zero Blog Post Today’s CPU vulnerability: what you need to know US-CERT Meltdown and […]
Continue Reading