Ransomware, data theft and leaks.
I do not plan on making this a ransomware-focused blog, but let us be honest, ransomware is just so prevalent that you cannot escape it. After my last blog and from private discussions, people working incident response cases in ransomware often are faced with the question: “When will the threat actor announce the attack and leak stolen data?”
Trying to answer this question is hard, as an external observer like myself does not have visibility into incidents or process attackers follow. All I can rely on is the data seen publicly and the claims threat actors make. Once again I turn to my data collection from the the past year and I can create a resource – COLT (Compromise to Leak Time). This number, expressed in days, helps answer that question. Think of it as a smoking gun for a ransomware incident. The moment you see the smoke, the gun fired and every person learns that something has happened.
Due to limited data sets I am only able to create a reliable number for two ransomware groups: DarkSide and PYSA/Mespinoza. Both groups are self-reporting the date they breached a victim and comparing it to the time they announce the victim, we can calculate a delta – COLT.
Let’s crunch the numbers.
DarkSide
For this ransomware group I reviewed 84 data leaks published on their leak blog. The first time the group claims to have compromised a victim was August 8th, 2020. This victim was announced on the blog on August 19th, giving us a first COLT of 11 days. Looking at the most recently announced victim, we see a compromise on April 22nd and a publication on April 28th, a COLT of only 6 days.
Looking at all data points, we have to following numbers:
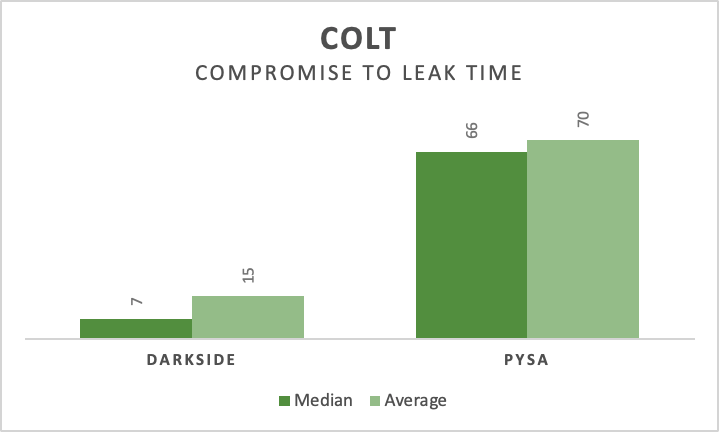
- COLTmedian: 7 days
- COLTaverage: 11 days
This is a pretty quick turnaround from compromise, data exfiltration, system encryption, ransom extortion chat and publication. The largest COLT for a victim of DarkSide is at 93 days, while the shortest is at 0 days, meaning the victim was published the same day it was hacked. DarkSide lists 6 victims with a COLT of 0 days.
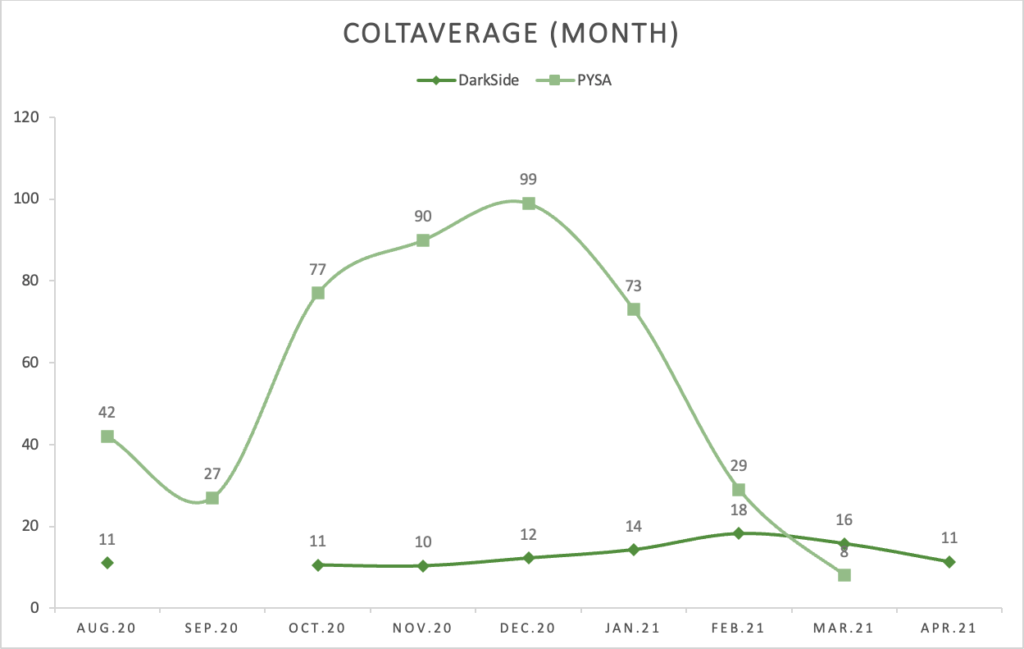
Another interesting observation with DarkSide can bee seen when we look at the data by month. Here the COLTaverage lies between 10 days (November 2020) and 18 days (February 2021). We can also see that the operators took a break in September, as no victims were reported being compromised or added to the data leak blog.
PYSA/Mespinoza
For this ransomware group I reviewed 115 data leaks published on their leak blog. A problem in this analysis might be that PYSA seems to mix up dates and ordering them the wrong way around (12/04 vs 04/12), wrongly self-reported compromise dates (several victims publicly state different attack dates). Additionally, PYSA publishes several victims in a batch, making it difficult to have really reliable numbers.
For PYSA we have the following result:
- COLTmedian: 66 days
- COLTaverage: 70 days
The range is between 0 and 452 days (still might contain errors). If we only look at the data for compromises from the past 6 months (November 2020 to April 2021), we get 49 victims and the COLT numbers of:
- COLTmedian: 86 days (+20)
- COLTaverage: 85 days (+15)
This shows us that PYSA got slower in announcing their victims. The range however gets narrower and is between 7 to 130 days.
What observations can you make from this data? Have you worked incidents and would like to share your data? Let me know, I am always eager to hear other opinions and feedback.
Visualizations
Update 2021-05-03
The MISP project team has added the COLT numbers for DarkSide and PYSA into the ransomware galaxy.
Hello, nice analysis ! I have two questions and one suggestion to stimulate the discussion and thinking.
Is there a correlation between COLT and the size of exfiltrated data ?
Are there clusters of COLT that could indicate affiliates working at different speed ?
Another data point which could be useful is the moment when the attackers decided to encrypt the victim’s files, because COLT might be influenced by the time attackers spent on network compromise and data exfiltration.
Best regards
Hi JM, excellent question. I have not yet looked at the data of this. Given that my COLT numbers are based on information shared by the ransomware group themselves they must have felt confident enough about the stolen data to trigger the ransomware and lose access.
COLT is in big parts driven by the actor, if undetected. Once detected, they trigger the ransomware and shorten COLT.