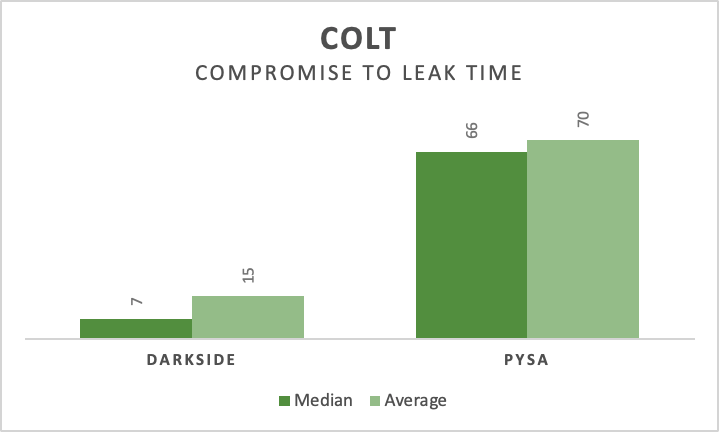
Ransomware, data theft and leaks. I do not plan on making this a ransomware-focused blog, but let us be honest, ransomware is just so prevalent that you cannot escape it. After my last blog and from private discussions, people working incident response cases in ransomware often are faced with the question: “When will the threat […]
Continue ReadingRansomware and Data Leak Site Publication Time Analysis
Learn at what times ransomware and data leak site operators are publishing victims on their dark web sites.
Continue ReadingMalicious Attachment Analysis Script
I love collecting malicious emails, samples and trying to make sense of it, create context and share back with the community. One way I do so is by sharing malicious email attachments to MalwareBazaar and VirusTotal and including context such as email sender, subjects and date information. Since doing that, I have heard a few […]
Continue ReadingFrom Russia with Love (and some help by Google)
Through some threat hunting on some OSINT platforms, I discovered a website hosting an image file named “image293.jpg” (6b872d1e949bd9d111168692301414bb685dc5c262ffae6f55f34c8041de0f5f VT | HA | ANY.RUN | Joe Sandbox). Trying to download the file shows that it is a redirect to Google’s short-url service goo.gl. From the link’s statistics page we can see that over 8500 redirects have been […]
Continue ReadingCompromised Arabic Domain Hosting Malicious Files
Today I came across a suspicious Word document when browsing Hybrid Analysis (which is always fun to see what is going on). The document caught my eye for the single reason that it was called “swift message 1.docx” (c07fb4ab07e439463117cd7d060109cb814d928304e8828c3884ac2b88fece78). Since I work for a bank, I always have an urge to checkout banking related stuff […]
Continue Reading“You order form:[RANDOM] from 06/05/15 recived;” Attachment Analysis
Today I came across a message, which was rather interesting. The mails were received with different subjects, random company names in them as well as random attachment names. The attachment is a Word document with the “*.doc” extension (never a good sign). Quickly analysing shows that the Word document contains a Marco script, which, when executed, […]
Continue Reading