Today marks a big day for the security research and protection effort here at vulnerability.ch: We just created and shared our 100th event with the wider MISP community.
Thanks to the inclusion of our research at the MISP community provided by CIRCL, we have been able to share and consume indicators of compromise (IOCs) from various malware campaigns, share knowledge about indicators with peers and other communities and allow for a better protection and understanding of the threat landscape.
Thanks to our own Switzerland based email and spam trap systems, we are able to obtain malware targeting Swiss corporations, analyse malicious attachments and report IOCs for abuse and takedown. This all is made possible thanks to some great tools and resources the team has access to:
- URLhaus by abuse.ch for tracking and reporting of malicious URLs
- ReversingLabs, a platform that allows us to identify related samples and extract additional file information
- Any.Run to interact with malicious files
- Intezer to classify samples in to malware families
- VirusTotal for reporting suspicious files to the antivirus community
- Twitter is invaluable for reaching out to peers, friends and partners for collaboration
Lessons Learned for Swiss Businesses
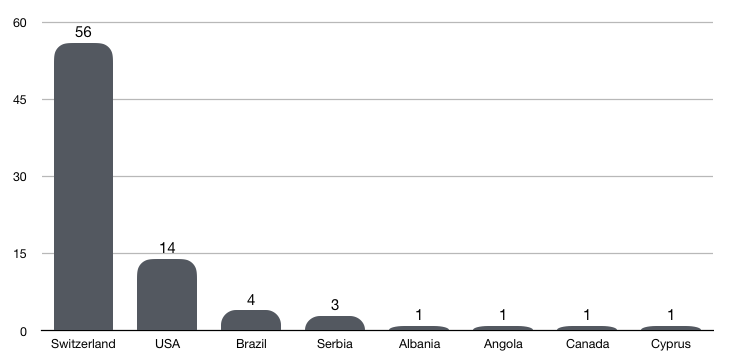
With our private spam traps and tagging technique, we can identify which sector/business was targeted in a malware campaign. From that we learned that actors can be highly persistent and tend to switch malware tools, if they are not successful at first. We have been monitoring one email address, that has received a wide variety of malware families, like FormBook to Pony/Fareit to LokiBot, just to steal sensitive information from the owner of that email address.
The attached malware comes in a large variety of formats, from the all persistent Office Word document with macros, to binaries (exe) in archive files (rar, ace, zip) to the most curious attachment formats like “.daa” (a proprietary format by PowerISO).
It is highly recommended that small and medium business (in any sector) start to block incoming email, especially for attachments that are not used for business needs (e.g. “.iso”, “.img”, “.vbs”, “.exe”) and also make sure that archive formats can be inspected and blocked. Further make sure that your Microsoft Office settings are set to not run Macro code when a document is opened (Microsoft article in English, German and French).
Further make sure that you train your employees in the usage of email and internet at the workplace. Make sure to always stay suspicious on emails, that are unexpected or coming from unknown contacts (or from contacts but with unexpected attachments). For more information please check the recommendations that MELANI has shared on their website in English, German, French and Italian.
Finally make sure that you share information with your employees, who to contact if a suspicious email was received or opened.
Appendix – Malware Families
| Malware Family | Amount |
| Loki Password Stealer (PWS) | 20 |
| Pony/Fareit | 16 |
| FormBook | 6 |
| GandCrab | 4 |
| HawkEye | 5 |
| Hancitor | 3 |
| Nanocore RAT | 3 |
| Remcos | 3 |
| AdWind RAT | 2 |
| AZORult | 2 |
| Gozi | 2 |
| Trickbot | 3 |
| Agent Tesla | 1 |
| Cobalt Strike | 1 |
| DanaBot | 1 |
| DarkComet | 1 |
| Dridex | 1 |
| Emotet | 1 |
| Imminent Monitor | 1 |
| ISR Stealer | 1 |
| Netwire | 1 |
| Retefe | 1 |