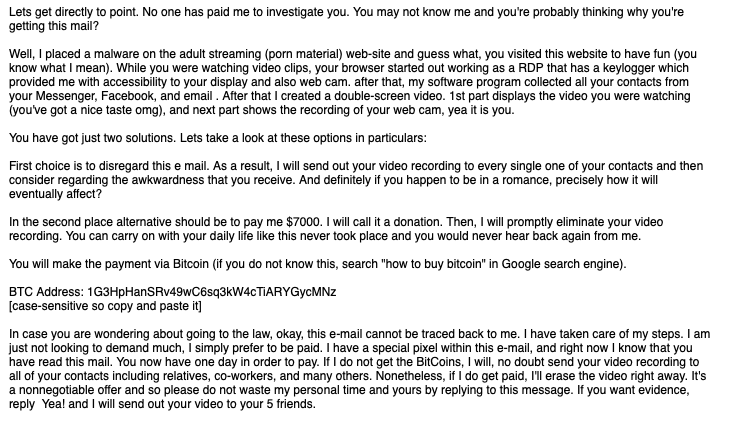
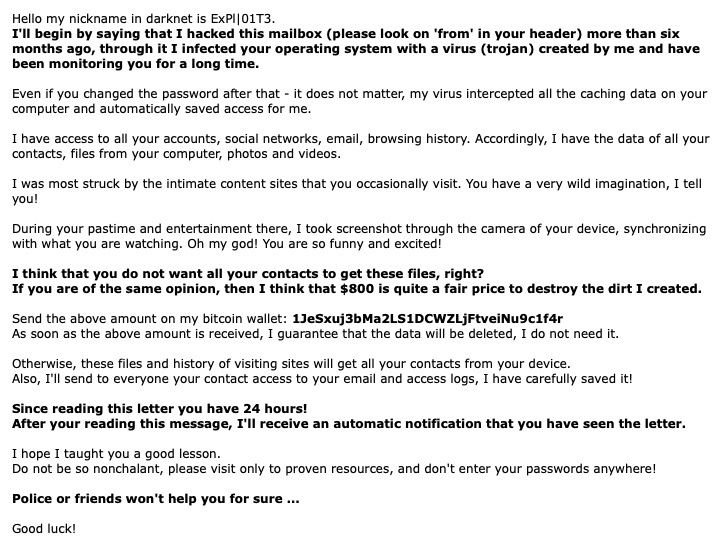
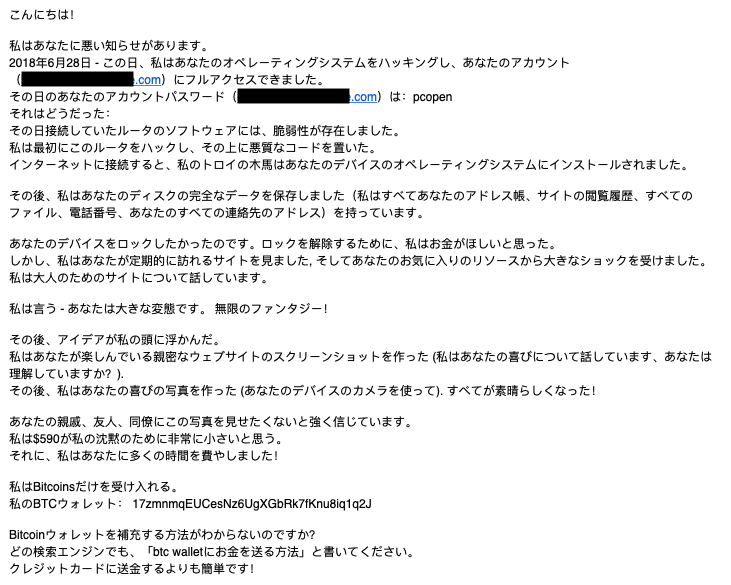
For the past few months (it started in July 2018), I have been collecting Bitcoin wallet addresses from so called “extortion” or “sextortion” emails. The addresses have been added to my MISP server and is shared with other researchers to investigate or detect additional mails.
CIRCL now has used the data to generate an analysis of how much money was transferred into and out from those wallets:
What’s the economical gain for an attacker to send #sextorsion emails? We review all the balances of the notified BTC addresses in @MISPProject (Thx @cocaman) 500K EUR cashed out & 804K EUR received from victims. The view is partial but gives an idea of the economical incentive. pic.twitter.com/fHU6u2bdLk
— CIRCL (@circl_lu) January 20, 2019
As you can see, the 1300+ BTC addresses generated almost BTC 165, of which a total of BTC 131 have already been spent. Pretty substantial for “sending emails” and making empty threats to victims. In a time where we see 773 million credentials leaked (or re-leaked), this could show a possible answer to “what can attackers do with my email and password?”.
If you are interested in the BTC addresses, check the MISP event “5b563598-96cc-4700-b739-28f8c0a80112“, shared across various MISP instances. If you don’t have access, let me know and I can share the data with you. And if you want to connect your MISP instance, please also let me know.
The tool used to generate the statistics can be found on Sascha Rommelfangen’s Github site.