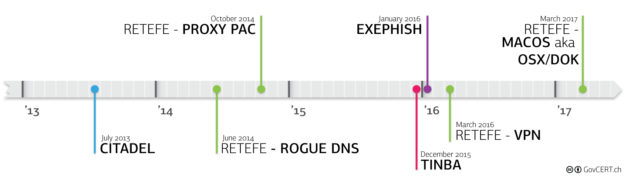
I recently took a closer look at Retefe because they seem to have abandon the short-lived “SmokeLoader”-phase and moved back to “socat.exe” and the TOR-network. The original delivery method is by mail spam, sending an Office document (either a docx or xlsx attachment) with an embedded OLE object (the malicious .exe file). If the victim […]
Continue ReadingExtracting Payload Urls From Office Docs With CyberChef
For several months now, Emotet has been using various Office document fields (e.g. Author, Comments) for “hiding” their PowerShell code to download the exe payload. The actors behind the malware often change little things in their code to make automated extraction of urls harder. On November 8th a friend asked me for help on a […]
Continue Reading