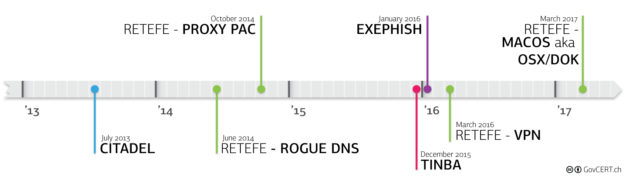
I recently took a closer look at Retefe because they seem to have abandon the short-lived “SmokeLoader”-phase and moved back to “socat.exe” and the TOR-network. The original delivery method is by mail spam, sending an Office document (either a docx or xlsx attachment) with an embedded OLE object (the malicious .exe file). If the victim […]
Continue ReadingExtracting HTML Body From Firefox Cache
Today I was asked for a copy of a website that was already nuked before the analysis was completed. No online platforms has yet picked up a copy and VirusTotal did not show a hash for the download. Trying to come up with a solution for this problem, I remembered that browsers often keep a […]
Continue ReadingExtracting Payload Urls From Office Docs With CyberChef
For several months now, Emotet has been using various Office document fields (e.g. Author, Comments) for “hiding” their PowerShell code to download the exe payload. The actors behind the malware often change little things in their code to make automated extraction of urls harder. On November 8th a friend asked me for help on a […]
Continue Readingvulnerability.ch now HSTS preloaded
As of September 8th, 2015 this website has been added to the HSTS preloading list of Google Chrome. I expect Firefox to follow soon. This ensures that all connections from your browser is sent over encrypted HTTP, even when you try to connect with http://vulnerability.ch. You can check HSTS-Settings in Chrome under: chrome://net-internals/#hsts How to add […]
Continue ReadingHack of the Day: Xing
Hack of the Day – Xing I have been using Xing for close to eight years. And I have tried the Premium feature for a little while. But luckily my card run out and that solved the hassle ton cancel my account 😉 However, have you every seen this on your front page: The “Profile Visitors” […]
Continue ReadingWhy Password Re-Use Is Bad For You
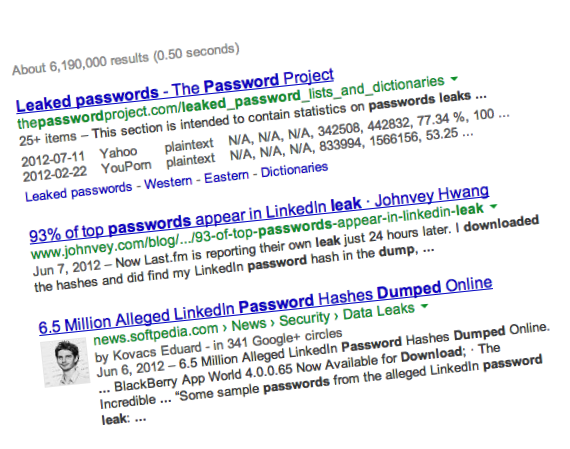
Every now and than, a website on the Internet gets hacked and sensitive data of its users are stolen. Sensitive data can be anything, from your email address, to your birthday, social security number, credit card details or your password (either in hashed, encrypted or plain text form). While all this data is critical to […]
Continue Reading