Through some threat hunting on some OSINT platforms, I discovered a website hosting an image file named “image293.jpg” (6b872d1e949bd9d111168692301414bb685dc5c262ffae6f55f34c8041de0f5f VT | HA | ANY.RUN | Joe Sandbox). Trying to download the file shows that it is a redirect to Google’s short-url service goo.gl.
From the link’s statistics page we can see that over 8500 redirects have been performed (and rapidly climbing):

Most of the visitors have been coming from Poland, followed by Russia:

The redirect forwards a visitor to a Google Docs hosted file. Again, the filename tricks the user to think the file is a JPEG image, but it is actually a Windows executable:
image293.jpg: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Window
From the executed processes, we see that the file is being installed as “steamerrorreporter.exe”, a way to hide itself from prying eyes.
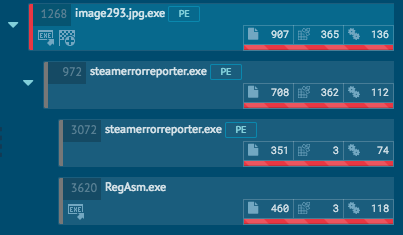
The malware also gets executed at each restart by adding itself to the Windows autostart process.
Sadly I do not know yet, what malware it is, various analysis are not conclusive. Most likely it will be information stealer. Further I have no idea what the initial vector is…
The IP address (31.31.196.182 VT | RiskIQ) hosting the domain “imagescreen[.]pictures” has a bad history, hosting various bad domains, phishing and files in the past few days.
The Google (goo.gl & Docs) links have been reported and get removed soon I hope.
Indicators of compromise
hXXp://imagescreen[.]pictures/image293[.]jpg
imagescreen[.]pictures
31[.]31[.]196[.]182
hXXps://goo[.]gl/9Z7RJj
hXXps://doc-0s-1s-docs[.]googleusercontent[.]com/docs/securesc/ha0ro937gcuc7l7deffksulhg5h7mbp1/9rih0c7lgvoqg01lbscujcso2kdsnhhe/1515312000000/03917946903997176890/*/1UYuf6eIeJnFkhI85KcdN4rwYLR9ypV2U?e=download
6b872d1e949bd9d111168692301414bb685dc5c262ffae6f55f34c8041de0f5f
passivetotal_31-31-196-182_resolutions
Update 2018-01-07 5:30pm
Thanks to some awesome friends around the globe, we were able to identify the sample as a variant of “Steam Stealer“.
Steam Stealer, a growing family of malware that hackers are using to steal credentials for Valve Corporation’s Steam online gaming platform, for eventual resale on the black market
Several runs in the various sandboxes didn’t show any activity of the malware, which is a first indication that the sample is aware of its surrounding. Might be worth checking this out…
Update 2018-01-08 7:15am
And the “goo.gl”-shortlink is gone (after over 18’000 clicks)